Joomla Vulnerability Problem
I should be honest I am not big fan of Joomla, I don’t really like the quality of their code base and the architecture of their solution at least when it is in comparison with the current state of WordPress for example.
Anywho 2 days ago Joomla gave me quite a scare. One ‘hacker’ – kid with nothing better to do – exploited one dangerous Joomla vulnerability.
There was apparently BUG in the file upload and in the com_media administration component, which BOTH bypass the user session check.
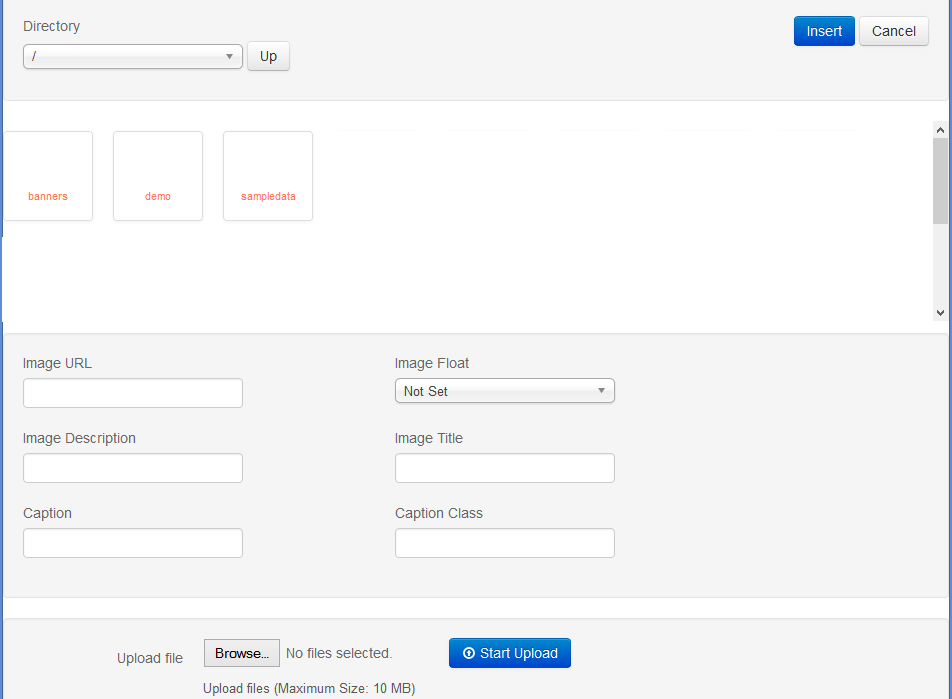
This Joomla vulnerability give you permission to upload files to every folder in the site, which could be quite dangerous ‘feature’ if the site was in the hands of better (real) hacker.
First the media library present you with nice window which you can reach on: http://example.com/index.php?option=com_media&view=images&tmpl=component
Afterwards the upload file functionality permits you to upload file without any authentication.
This bug is so obvious and so dangerous that I am only let to believe that it was left on purpose.
Joomla Vulnerability Solution
Now let’s try to fix this bug:
1. Check if you have everywhere but mainly in the file /administrator/components/com_media/media.php:
defined('_JEXEC') or die;
2. Restrict the assess for guests:
// Access check: is this user allowed to access the backend of this component?
if (JFactory::getUser()->guest) {
return JError::raiseWarning(403, JText::_('JERROR_ALERTNOAUTHOR'));
}
Or if you prefer 404 message
// Access check: is this user allowed to access the backend of this component?
if (JFactory::getUser()->guest) {
return JError::raiseWarning(404, JText::_('JERROR_LAYOUT_PAGE_NOT_FOUND'));
}
Maybe that is not the most elegant solution but it still fixes successfully one really dangerous security hole.
If you have better suggestions I will be happy to hear them 
UPDATE:
More Joomla Vulnerability examples you can find under:
http://www.cvedetails.com/vulnerability-list/vendor_id-3496/product_id-16499/Joomla-Joomla-.html
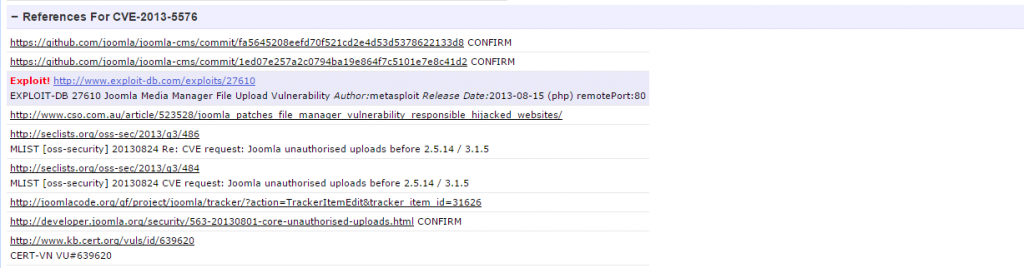
If you want to test the ones that are already exploited go to specific vulnerability and scroll down to references:
There you can find Metasploit code or manual explanation of the exploit.
You can also try the direct link: http://www.exploit-db.com